Rapidly Deploy IoT Solutions
End-to-end, flexible, scalable, and secure
Any Sensor, Any Cloud, Any Network, Any Platform or Application
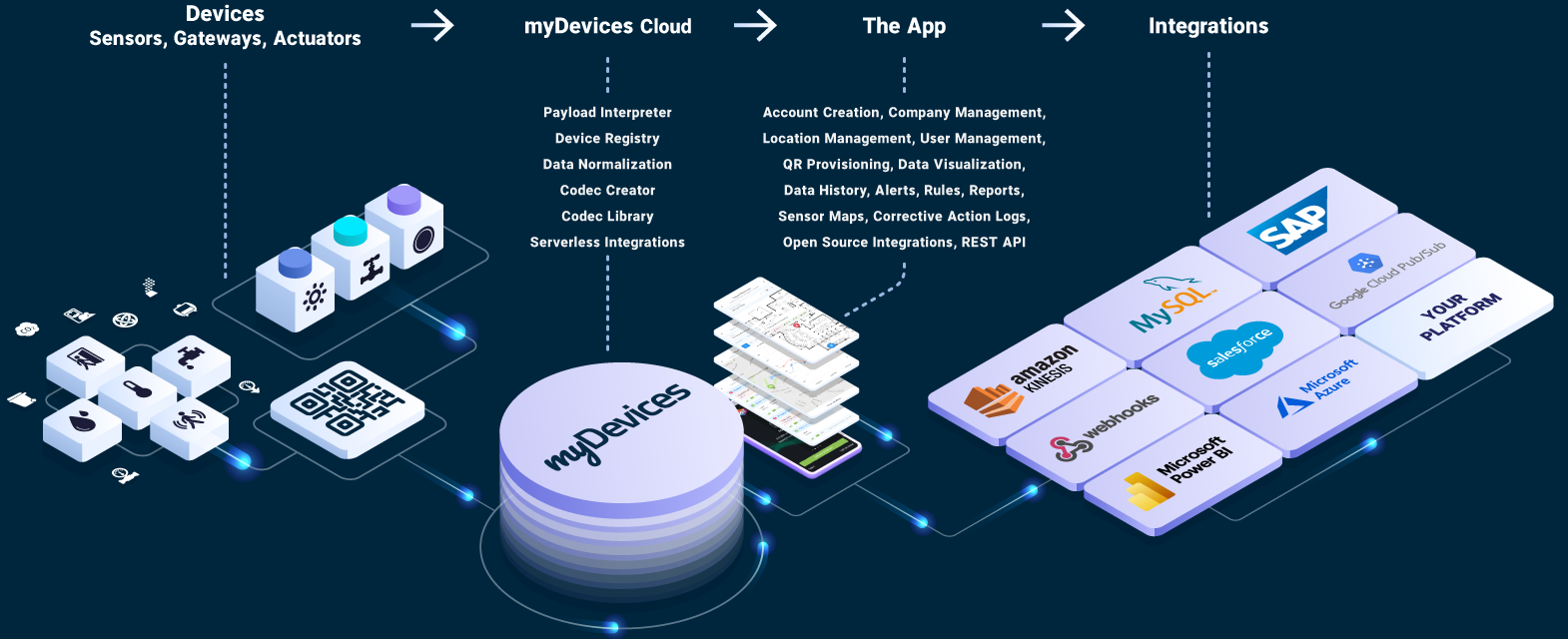
Microservices Architecture
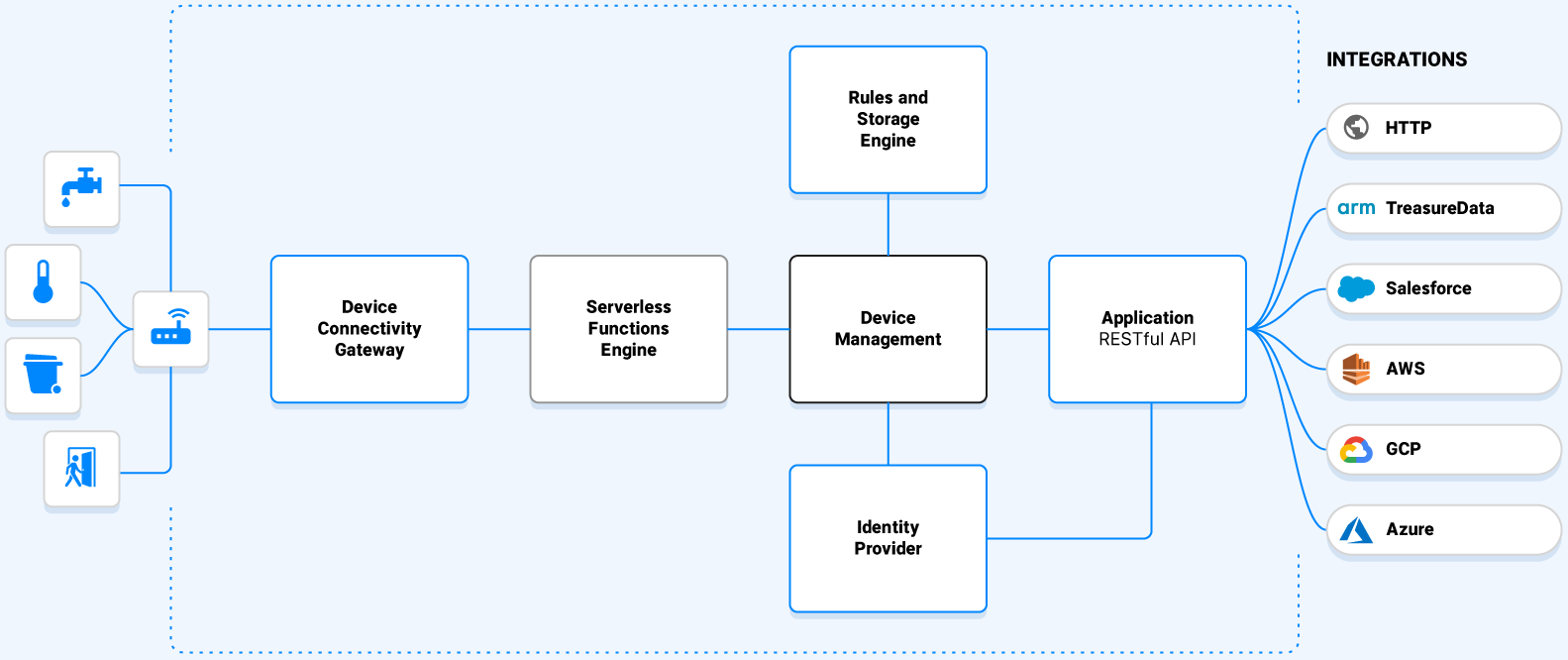
Platform Capabilities
Accelerate time to market with everything you need to securely and quickly deploy finished solutions for any industry
Device Connectivity Gateway
Maintains encrypted connections with devices supporting HTTP and MQTT protocols. Receives traffic from LoRa Network Servers and data stream from other IoT Clouds.
Serverless Engine
All-purpose serverless computing or function as a service (FaaS) provides codecs and integrations online editing. Decodes and normalizes uplink device data and encodes downlink commands simplifying the deployment of integration functions.
Device Management
Manage device registry, configuration, provisioning, and FOTA scheduling and batching. Easily de-register and re-register devices via LNS Switch. Stores LoRaWAN keys and SSL/TLS certificates with access to real-time data insights.
Storage
Industry-leading performance with large data volume storage to easily query billions of rows of telemetric and historic data. Fast ingest of millions of data points per second, plus vertical and horizontal scalability powered by data streaming processing engine.
Rules Engine
Scalable and advanced rules engine with advanced setup and configuration with different conditions and actions that are also leveraged with our integrations.
Identity Provider
Authentication & authorization system that supports OAuth 2.0 & OpenID Connect protocols, external User Federation (LDAP & Active Directory), external identity providers (Idp) for Google and Microsoft, and SSO SAML. Enterprise-grade user management.
Applications
Supports web and native iOS and Android applications with multi-tenant capabilities. REST API can be used to extend application features.
Integrations
Low effort integration setup and configuration. Connectors send data to 3rd party integrated applications such as Arm, Azure, Salesforce, Tableau and more for visualization, reporting analytics, BI, machine learning, and business workflows. Build your own data connector and integration with our REST API.
LoRa Technology
LoRa Technology has been named the de facto choice for LPWAN connectivity for long range, low power IoT solutions.
Any Cloud
Choose the right IoT enterprise cloud infrastructure for your business needs

Amazon Web Services

Microsoft Azure

Google Cloud
End-to-End Security
The myDevices IoT platform is secure from the edge to the application layer through the cloud. The security is composed of LoRaWAN Network Security at the edge, TLS to the cloud and SAML at the application layer.
On the edge: LoRaWAN Stack
The LoRaWAN stack is built on top of LoRa modulation (PHY) and adds a full security layer with device identity, authentication, and authorization. The stack uses symmetric AES128 keys as described in IEEE 802.15.4/2006 Annex B. MAC for encryption. These keys are used for layer related frames encryption using a Network Session Key (NWKSKey) while the applications frames are encrypted using an Application Session Key (AppSKey). Similar to routers, the gateways used in a LoRaWAN can forward from and to the cloud using DTLS, TLS, or VPN without decrypting or knowing any of the keys.
In the cloud: LoRaWAN Network Server (LNS)
Within the LNS lies the registry of devices and gateways that transmits data to the cloud. Each device is identified with a couple of unique identifiers called the DevEUI and AppEUI. The AppSKey and NwkSKey are negotiated1 along with the regional regulation settings when the device joins the network. The last stage of the LNS is to forward all traffic to the myDevices Cloud using HTTPS (TLS/SSL).
In the application: myDevices Cloud
The myDevices Cloud is an IoT platform that supports different device connectivity protocols without compromising security. All communications such as database connections and service-to-service communications within the platform are encrypted. In addition, data is encrypted within the database, and we enforce rigorous access control list (ACL) for staff personnel and customer data. Our customer applications and backend system utilizes the standard OpenID Connect (OIDC) and SAML 2.0 protocols to initiate and authenticate any requests to our APIs. These protocols are the modern security standard for user-to-service and service-to-service communications.
TRUSTED BY




Deploy IoT Solutions
There are many ways we can work together!
Get in touch and learn how.